
The Rise of Hardware Trust in Blockchain
The evolution of blockchain technology is constantly pushing boundaries, with a critical focus on enhancing both security and scalability. Amidst this drive, hardware-based approaches are gaining prominence, promising a new era of secure and efficient decentralized applications. At the forefront of this innovation are Trusted Execution Environments (TEEs). These are specialized, isolated areas within a device’s processor, designed to ensure that data and code remain confidential and tamper-proof during execution. This hardware-level trust introduces a significant departure from traditional software-based security, which is inherently vulnerable to various attacks.
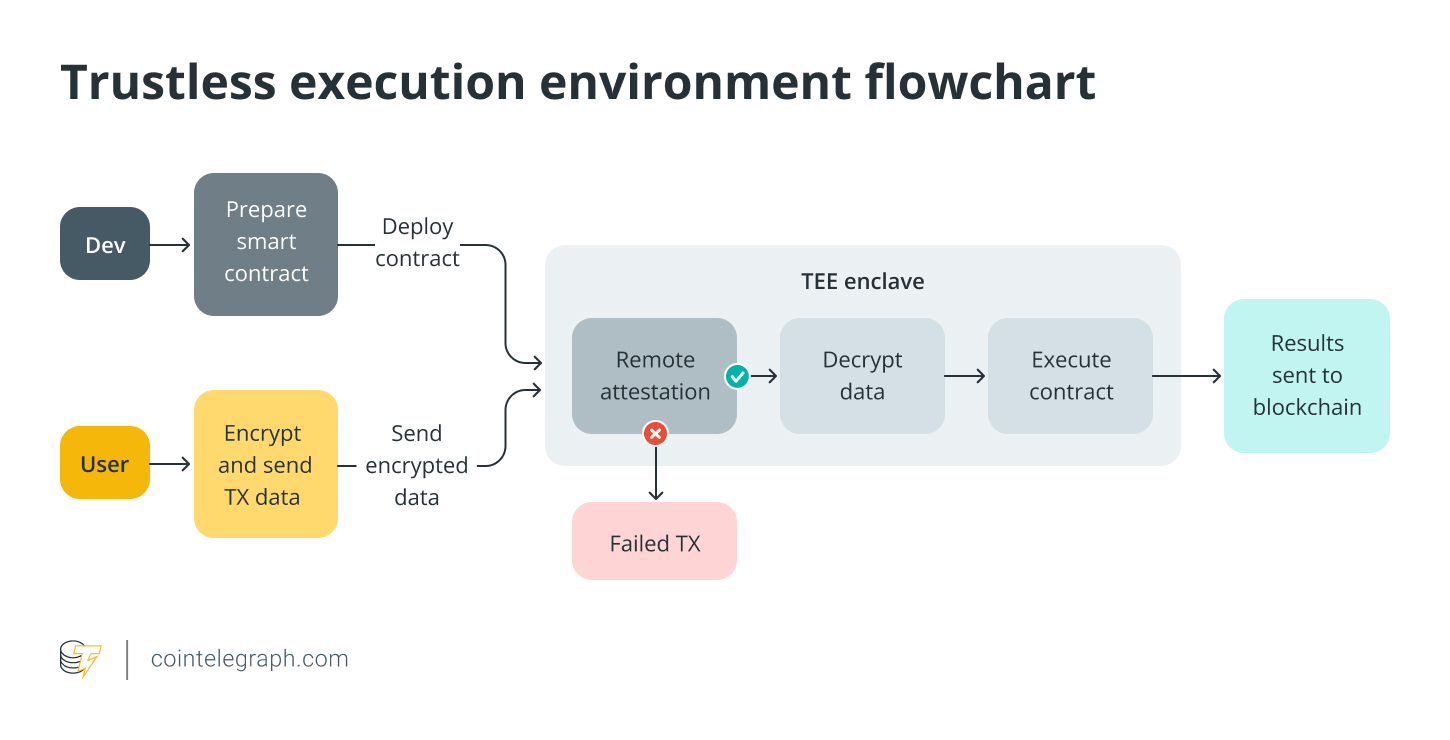
Understanding the Mechanics of TEEs
At their core, TEEs operate by creating a secure enclave, inaccessible to the rest of the operating system. This isolation is crucial for safeguarding sensitive operations like smart contract execution. A key component is the CPU’s ability to measure the Trusted Computing Base (TCB). This measurement, which includes boot firmware, the operating system kernel, and application binaries, is then saved in secure hardware registers. Subsequently, the CPU signs this measurement using a private attestation key, embedded directly within the CPU. This process produces a cryptographic attestation report. This report allows a remote verifier to confirm the enclave’s integrity and authenticity. This mechanism essentially allows the blockchain to “trust but verify” the computations happening within the TEE.

Key Use Cases: Beyond Privacy
While TEEs are instrumental in privacy-preserving applications, their utility extends far beyond. They are transforming how we approach scalability and off-chain computation. For example, TEE-enabled nodes can execute computationally intensive tasks off-chain and submit the results on-chain. This can significantly reduce gas costs and increase transaction throughput. Moreover, TEEs are being leveraged to build MEV (Miner Extractable Value)-proof blockchain infrastructure. Innovative projects are utilizing TEEs to build blocks within protected enclaves. This helps prevent front-running and other MEV attacks, contributing to a fairer and more efficient DeFi ecosystem.
Vulnerabilities and Considerations
Despite their robust design, TEEs are not without potential vulnerabilities. A significant concern lies in the trustworthiness of the TEE hardware manufacturer. For instance, Intel’s Management Engine (IME), found in most Intel CPUs, has been shown to contain serious vulnerabilities. Further risks can stem from government influence or accidental vulnerabilities, such as the Plundervolt attack, which exploited a dynamic voltage interface to induce computation faults within enclaves.
Layer-1 vs Layer-2: Implementing TEEs
The integration of TEEs into blockchain architectures can take two primary forms: Layer-1 and Layer-2 solutions. In a Layer-1 setup, consensus nodes replicate an encrypted version of each contract’s state. Each node then uses a TEE to decrypt, execute, and re-encrypt the transaction. While this approach offers enhanced privacy, it can lead to a smaller validator set due to hardware requirements. Alternatively, Layer-2 schemes, such as rollups, employ TEE computations secured through dispute resolution mechanisms. These can significantly improve scalability. However, interoperability can be compromised, as contracts might not seamlessly call each other across different Layer-2 machines.

Looking Ahead: The Future of TEEs
The future of blockchain applications is increasingly intertwined with the advancement and adoption of TEEs. As the demand for computationally intensive decentralized applications rises, especially in areas like decentralized AI, TEEs are poised to deliver high-performance, low-cost off-chain computation. This evolution signals a shift from solely privacy-focused applications to scalability-focused solutions, with the potential to reshape the blockchain landscape. The integration of TEEs is not just a technological upgrade but a paradigm shift, promising a more secure, efficient, and scalable future for decentralized technologies.


