
2025: A Year of Fewer, More Devastating Crypto Breaches
The cryptocurrency space in 2025 witnessed a paradoxical trend: fewer individual hacking incidents, yet the total value stolen remained alarmingly high. According to data released by blockchain security firm CertiK, the overall number of attacks decreased, a potential indicator of improved protocol-level security. However, this apparent progress masks a concerning evolution in the tactics employed by malicious actors.
The Rise of the Supply Chain Attack
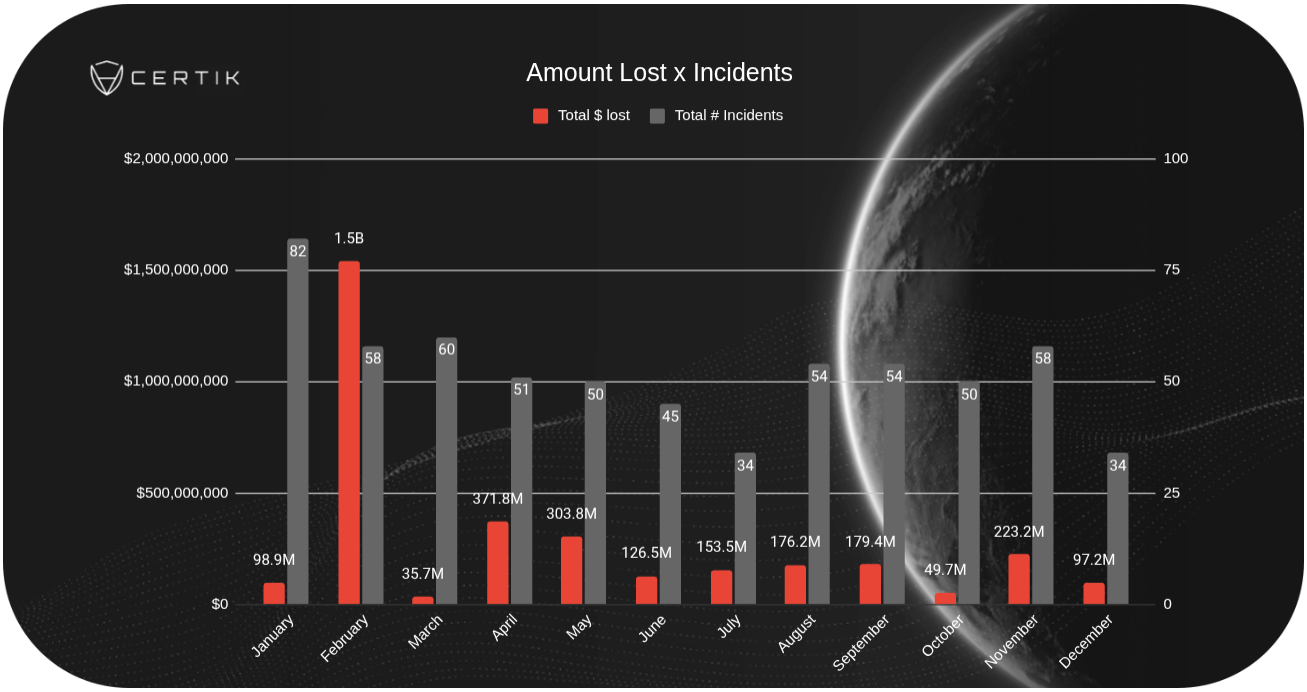
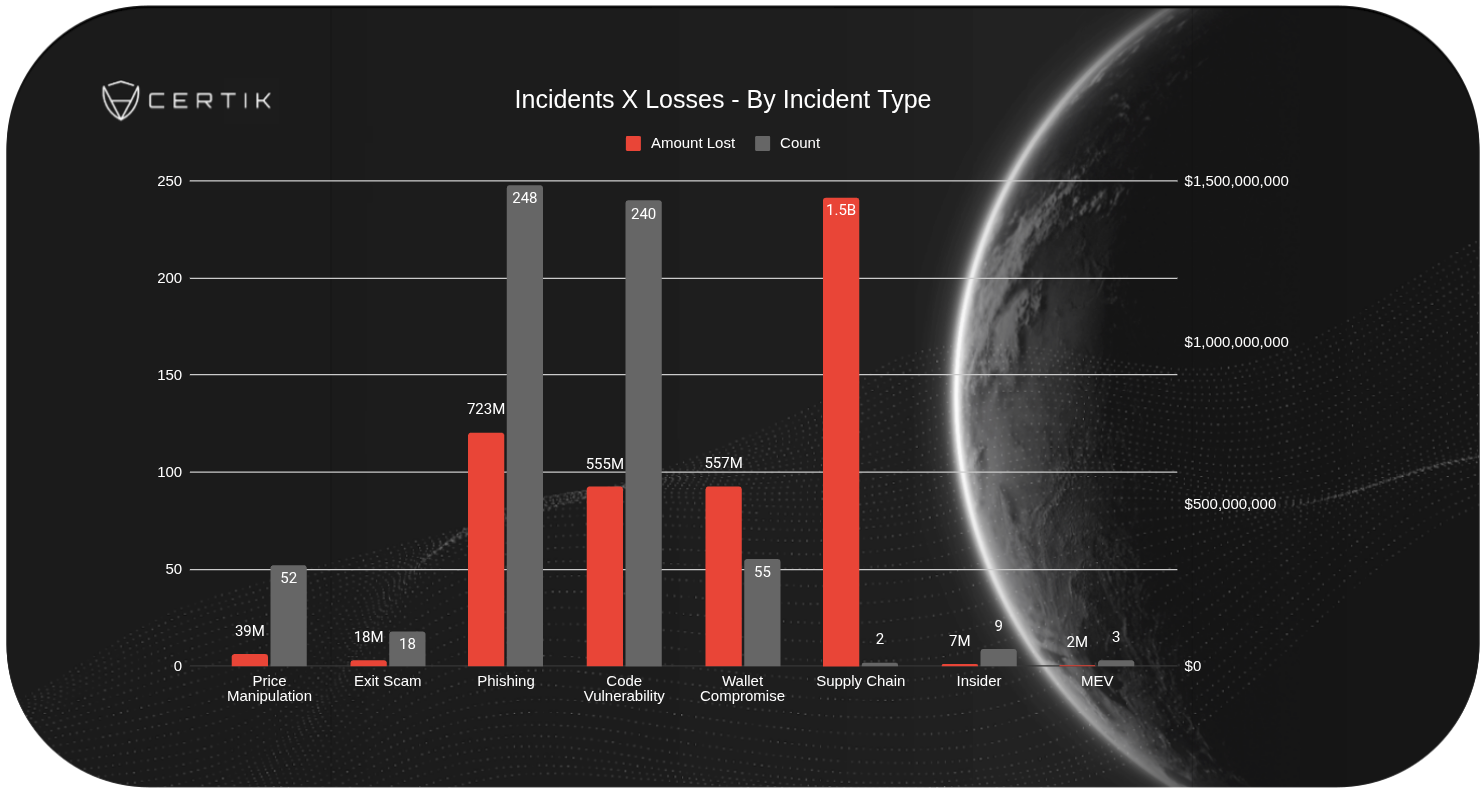
The most significant shift in the threat landscape was the emergence of supply chain attacks as the primary source of financial loss. These sophisticated exploits target the infrastructure underpinning the crypto ecosystem, rather than focusing on simple code vulnerabilities. The devastating Bybit hack, which alone accounted for a staggering $1.4 billion in losses, exemplifies this trend. This incident, along with another major supply chain breach, accounted for the bulk of the $3.3 billion stolen throughout the year.
Understanding the Numbers: A Closer Look
While the overall number of incidents dropped by 162 year-over-year, the average amount lost per hack surged to $5.3 million. This reflects the shift toward higher-value targets and more complex attack vectors. Interestingly, the median loss saw a decrease, which is a key metric less influenced by outliers like the Bybit hack. This divergence suggests that while some areas are improving, the most impactful attacks are becoming increasingly sophisticated and financially rewarding for the perpetrators.
The Growing Threat of Phishing and Social Engineering
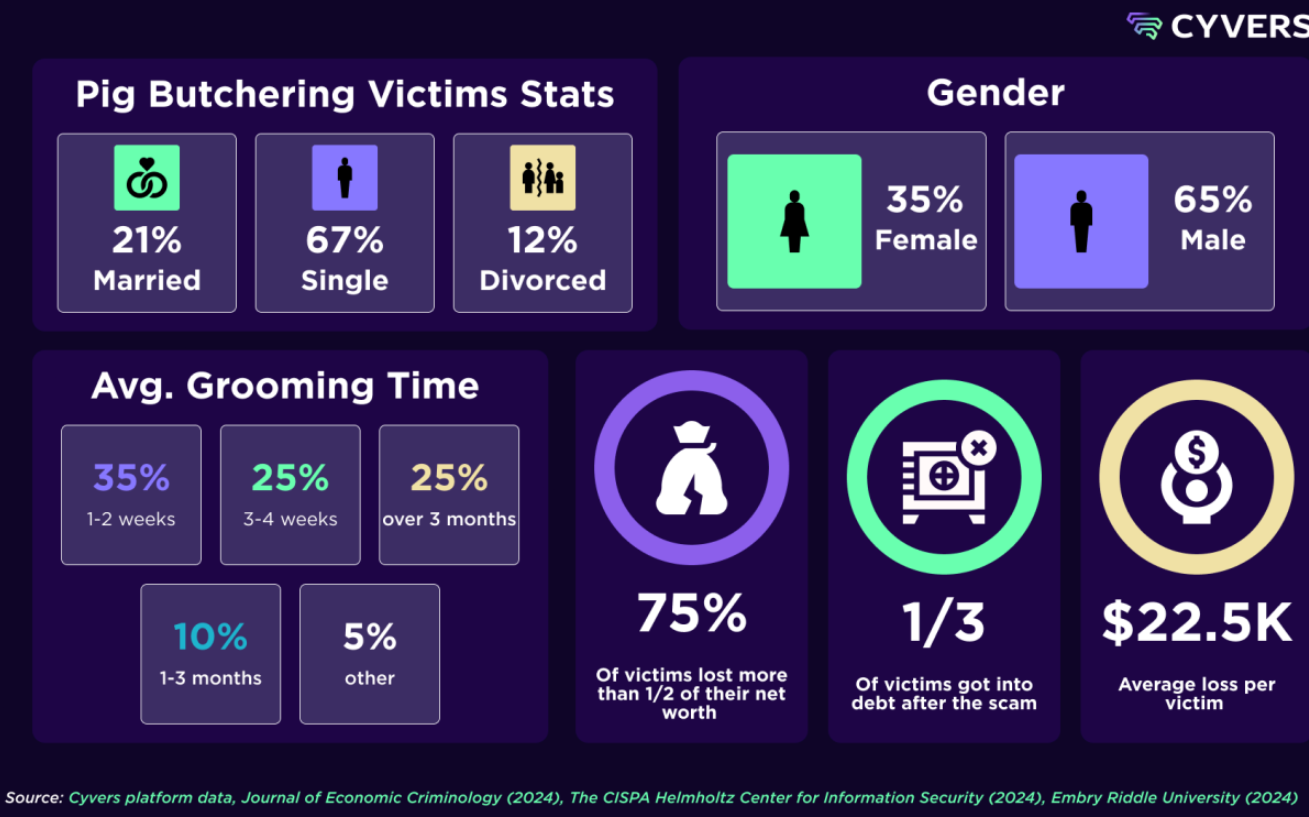
Beyond supply chain attacks, phishing scams and social engineering tactics continued to plague the crypto community. These attacks exploit human vulnerabilities rather than technical flaws, often resulting in significant individual losses. “Pig butchering” scams, in particular, proved to be a lucrative avenue for cybercriminals. These schemes involve prolonged emotional manipulation, with victims often groomed over weeks or even months before being tricked into transferring funds. The scale of these scams is massive, with previous years’ data indicating losses in the billions.
Implications and the Road Ahead
The changing dynamics of the crypto security landscape necessitate a proactive and adaptive approach. The decline in protocol-level vulnerabilities indicates that security teams are improving their defenses. However, the rise of supply chain attacks and social engineering requires a multi-faceted strategy. This includes strengthening infrastructure security, enhancing user awareness about phishing and social engineering tactics, and improving the ability to detect and respond to these increasingly sophisticated threats. The future of crypto security depends on staying one step ahead of the evolving tactics employed by malicious actors.
- Strengthened infrastructure security is critical.
- User education about phishing and scams is more important than ever.
- Improved threat detection and response capabilities are essential.


