
The Shadow of Third-Party Risk: Ledger‘s E-Commerce Data Breach
The world of cryptocurrency, while offering unprecedented financial freedom, also presents a unique set of security challenges. One persistent threat is phishing, a tactic that leverages deception to steal sensitive information. A recent incident involving Ledger, a leading hardware wallet provider, highlights the evolving sophistication of these attacks. A data breach at a third-party e-commerce partner, Global-e, exposed customer order information, which was then used to launch targeted phishing campaigns.

The Anatomy of a Phishing Attack
The breach itself did not compromise Ledger‘s hardware wallets or self-custody systems. However, the exposed data provided phishers with a crucial advantage: context. Armed with details like names, addresses, purchase history, and even product specifics, attackers could craft emails and messages that appeared legitimate, making it more difficult for users to distinguish between genuine communications and malicious ones.
How the Breach Unfolded
Global-e, the e-commerce partner, handles order processing and fulfillment for Ledger. This means they hold a treasure trove of personal data. The breach, which occurred in early 2026, exposed order-related information from customers who made purchases through this channel. Immediately, the attackers had the raw materials they needed to build convincing phishing campaigns. These campaigns often used urgency, claiming issues with orders, account verification problems, or firmware updates to pressure users into clicking malicious links or revealing their 24-word recovery phrase – the ultimate key to their crypto assets.
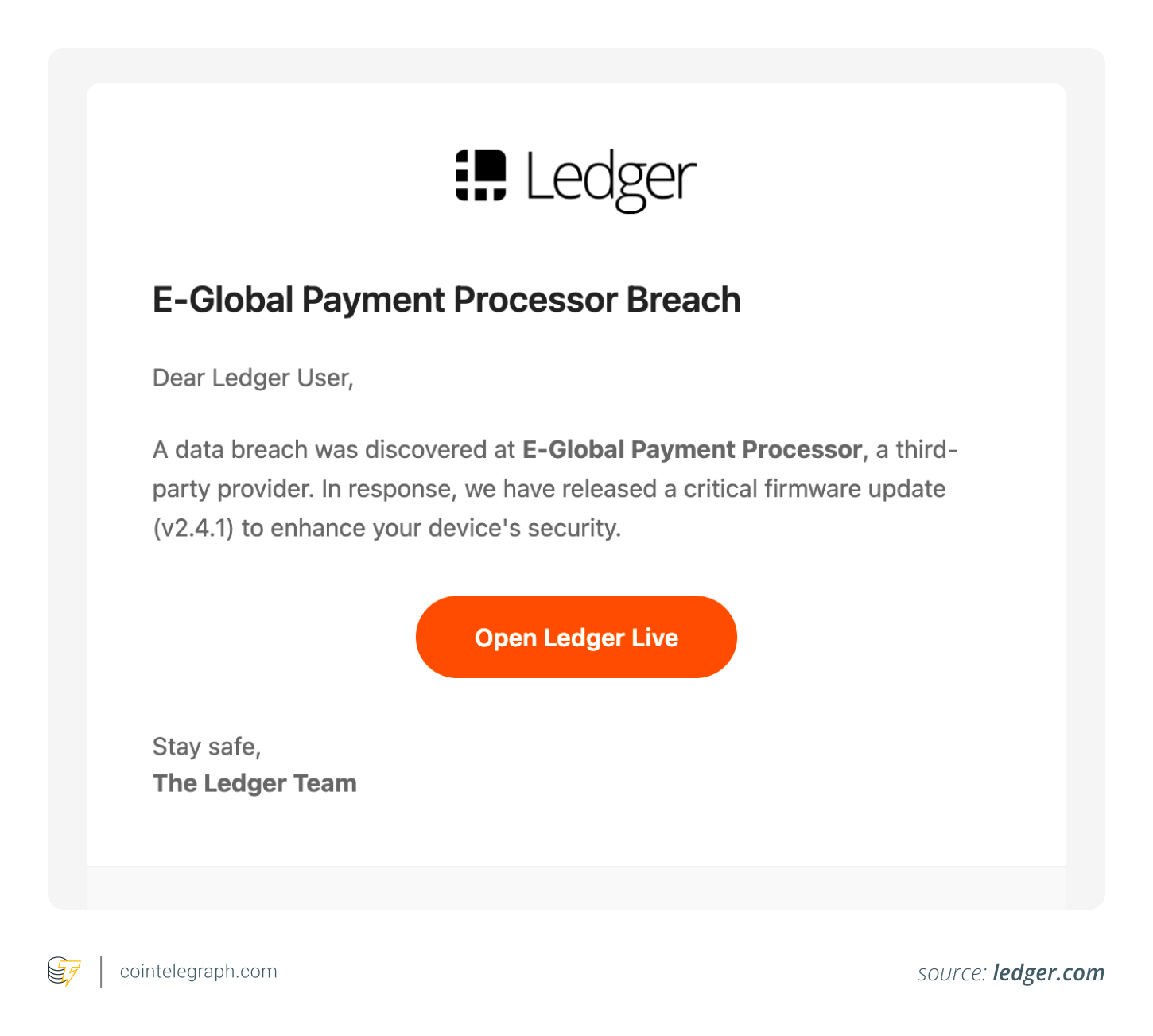
Key Takeaways for Crypto Security
This incident offers valuable lessons in crypto security. While Ledger’s hardware wallets provide robust self-custody, users must remain vigilant about the potential for social engineering attacks. Here’s what to keep in mind:
- Third-party risk is real: Even if your wallet provider is secure, the vendors they use can become a weak link.
- Context is key: Phishing attacks become far more convincing when they reference personal details.
- Always verify: Treat any unsolicited communication, especially those claiming urgency, with extreme skepticism.
- Never share your recovery phrase: Ledger will never ask for it, and it should only be entered directly on your device.

Protecting Yourself from Evolving Threats
The Global-e incident is a stark reminder that the security landscape is constantly evolving. Attackers are becoming more sophisticated, and they are constantly seeking new ways to exploit vulnerabilities. Being proactive and always being aware are the best defenses. Regularly check official Ledger resources for the latest scam advisories, and never hesitate to verify the legitimacy of any communication through official channels. The security of your crypto assets depends on a blend of secure technology and informed user behavior.
This incident highlights that self-custody isn’t just about the technology; it’s also about understanding and mitigating the risks associated with the broader ecosystem.


