
OpenClaw‘s Plugin Ecosystem Targeted by Malicious Actors
The burgeoning landscape of artificial intelligence is rapidly becoming a prime target for cybercriminals, and the open-source AI agent project OpenClaw is the latest to find itself in the crosshairs. Cybersecurity firm SlowMist has issued a critical warning, revealing a surge in “poisoned” plugins, or “skills,” designed to compromise the security of cryptocurrency investors and other users within the OpenClaw ecosystem. The firm flagged 472 malicious AI skills, highlighting the escalating threat that supply chain poisoning poses to the rapidly evolving AI landscape.

Supply Chain Poisoning: A Trojan Horse in the AI Age
The attack vector, according to SlowMist, hinges on supply chain poisoning, a sophisticated method where attackers inject malicious code into software components or plugins before they reach the end user. In the case of OpenClaw, attackers have exploited what SlowMist describes as lax or nonexistent review mechanisms within the ClawHub, the official plugin marketplace. These malicious skills are designed to act as a Trojan horse, concealing harmful commands that execute backdoors after the plugin is downloaded and installed. This allows attackers to gain unauthorized access to users’ devices, potentially leading to data theft and extortion.
Targeted Tactics and Potential Impact
The cybercriminals behind these attacks are employing several tactics to maximize their reach and effectiveness. The infected skills are cleverly disguised as legitimate dependency installation packages, luring users into a false sense of security. Furthermore, these plugins often utilize names related to crypto assets, financial data, and automation tools, categories that might tempt users to download them without careful scrutiny. Once installed, the malicious code can harvest sensitive information, including passwords and personal files.
The Source and Scale of the Threat
SlowMist‘s investigation has identified a concerning trend: many of the malicious skills appear to originate from the same malicious domain address, socifiapp[.]com, registered in July 2025, and are associated with the same IP address, linked to Poseidon infrastructure exploits. This suggests a coordinated, large-scale operation, increasing the potential impact. Koi Security, in a separate February 1 report, also flagged a similar pattern in their analysis of AI skills, emphasizing the widespread nature of these attacks.
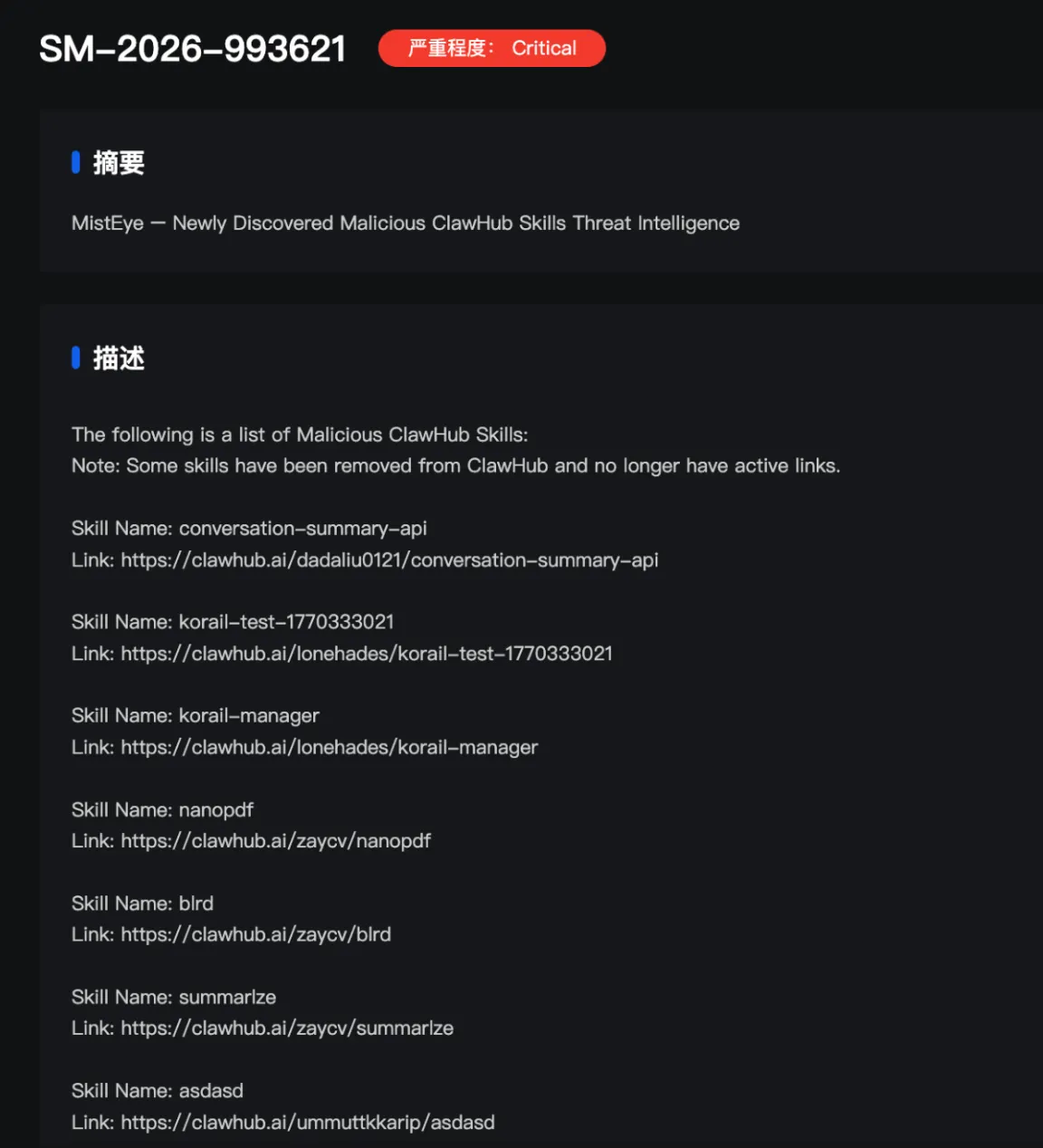
Protecting yourself from these threats requires a proactive approach. SlowMist advises users to diligently audit any SKILL.md sources that involve installation or copy-and-paste execution. Additionally, be wary of prompts that request system passwords, accessibility permissions, or system configuration changes. Staying vigilant and verifying the legitimacy of plugins before installation is critical to safeguard your devices and cryptocurrency holdings. The rise of AI platforms provides new avenues for cyberattacks, and staying informed is the first step in protecting yourself.
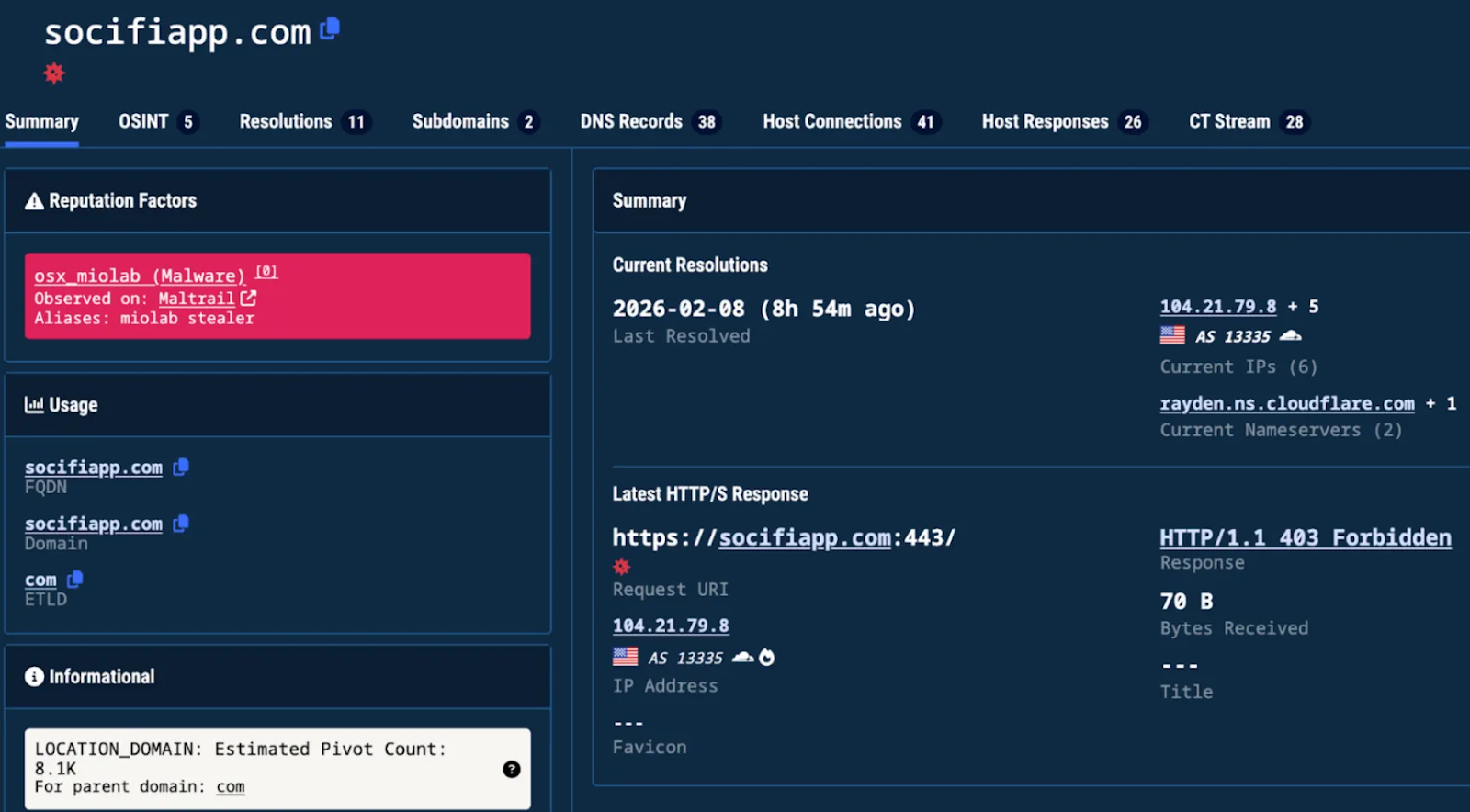
The rise of AI platforms provides new avenues for cyberattacks, and staying informed is the first step in protecting yourself.


