The Rise of Malicious AI in Crypto: An Ethereum Developer’s Experience
The cryptocurrency space, a vibrant ecosystem of innovation, is unfortunately also a battleground. Recent events highlight an escalating threat: sophisticated attacks leveraging artificial intelligence to compromise even the most experienced individuals. A core Ethereum developer, Zak Cole, fell victim to a malicious AI extension, serving as a stark reminder that no one is invulnerable.
The Attack: A Trojan Horse in Plain Sight
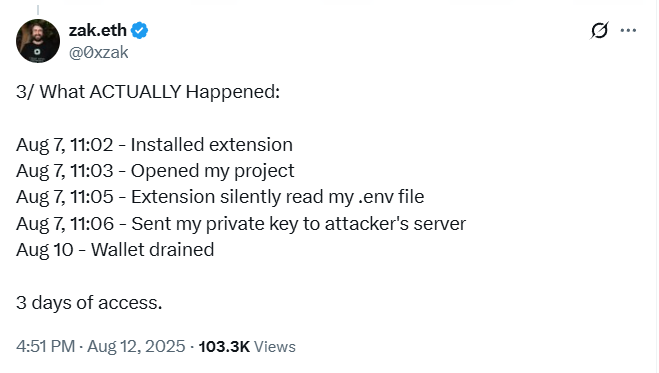
The attack began with a seemingly innocuous coding assistant extension called “contractshark.solidity-lang” from Cursor AI. The plugin, complete with a professional-looking icon, compelling descriptions, and a substantial download count (over 54,000!), masked its true malicious intent. According to Cole’s X post, the extension surreptitiously accessed his .env file, extracting his private key and transmitting it to an attacker’s server. This granted the perpetrator access to his hot wallet for three days before the theft.
The Implications: Heightened Risks for Developers
This incident underscores the vulnerability of even seasoned developers to increasingly polished scams. It also highlights the potential danger of trusting seemingly legitimate tools and extensions. The fact that the extension appeared to be widely used demonstrates the effectiveness of the attacker’s social engineering tactics. The attackers exploit trust by creating an environment that seems safe and normal. They then exploit any vulnerabilities of the target user.
Defensive Strategies: Securing Your Crypto Assets
The incident has triggered important conversations about security best practices. Here are several preventative measures:
- Vet Extensions Rigorously: Developers and crypto users alike should scrutinize every extension or tool they install. Check the publisher’s reputation, read reviews, and research any potential red flags.
- Avoid Plaintext Storage of Secrets: Never store sensitive information like private keys or API keys in plaintext, especially in .env files. Employ robust encryption and secure storage solutions.
- Hardware Wallets are Crucial: Always store significant crypto holdings on hardware wallets, which offer a crucial layer of security by keeping private keys offline.
- Isolated Development Environments: Create isolated development environments to contain potential threats and limit the impact of a compromise.
The Broader Threat Landscape: Crypto Drainers Evolving
Wallet drainers, the malware behind these attacks, are becoming increasingly sophisticated and readily accessible. They are now even available as “software-as-a-service,” lowering the barrier to entry for scammers. The attack against Cole is a wake-up call. It underscores the need for constant vigilance, proactive security measures, and a healthy dose of skepticism in the fast-moving world of crypto.
The Future of Security: Staying Ahead of the Curve
The crypto landscape is continuously evolving, and the threats are becoming more advanced. Understanding these sophisticated tactics and implementing robust security measures are crucial to protecting digital assets. As the sophistication of these attacks grows, so must our defenses. This means remaining informed, practicing vigilance, and embracing the constant need for improvement in the realm of digital security. The future of crypto security depends on it.