
The Shadowy World of MEV
Maximal Extractable Value, or MEV, represents a significant threat to blockchain users. It’s the process by which block producers and other actors manipulate the order of transactions to extract profits. This is achieved through techniques like frontrunning, where a malicious actor identifies a pending transaction and places their own transaction ahead to profit from the price movement. The lack of privacy in mempools, where pending transactions are publicly visible, is a key enabler of these MEV attacks. Ethereum, in particular, has been plagued by MEV, with substantial financial losses reported.
Enter Threshold Encryption: A Privacy Solution
To combat MEV, cryptographic solutions like threshold encryption have emerged. These methods encrypt transaction data before it enters the mempool, keeping it concealed until the transaction’s final inclusion. The Shutter protocol is a prominent example, being the first threshold-encryption protocol designed explicitly for this purpose. It’s live on Gnosis Chain, representing a practical application of the technology.
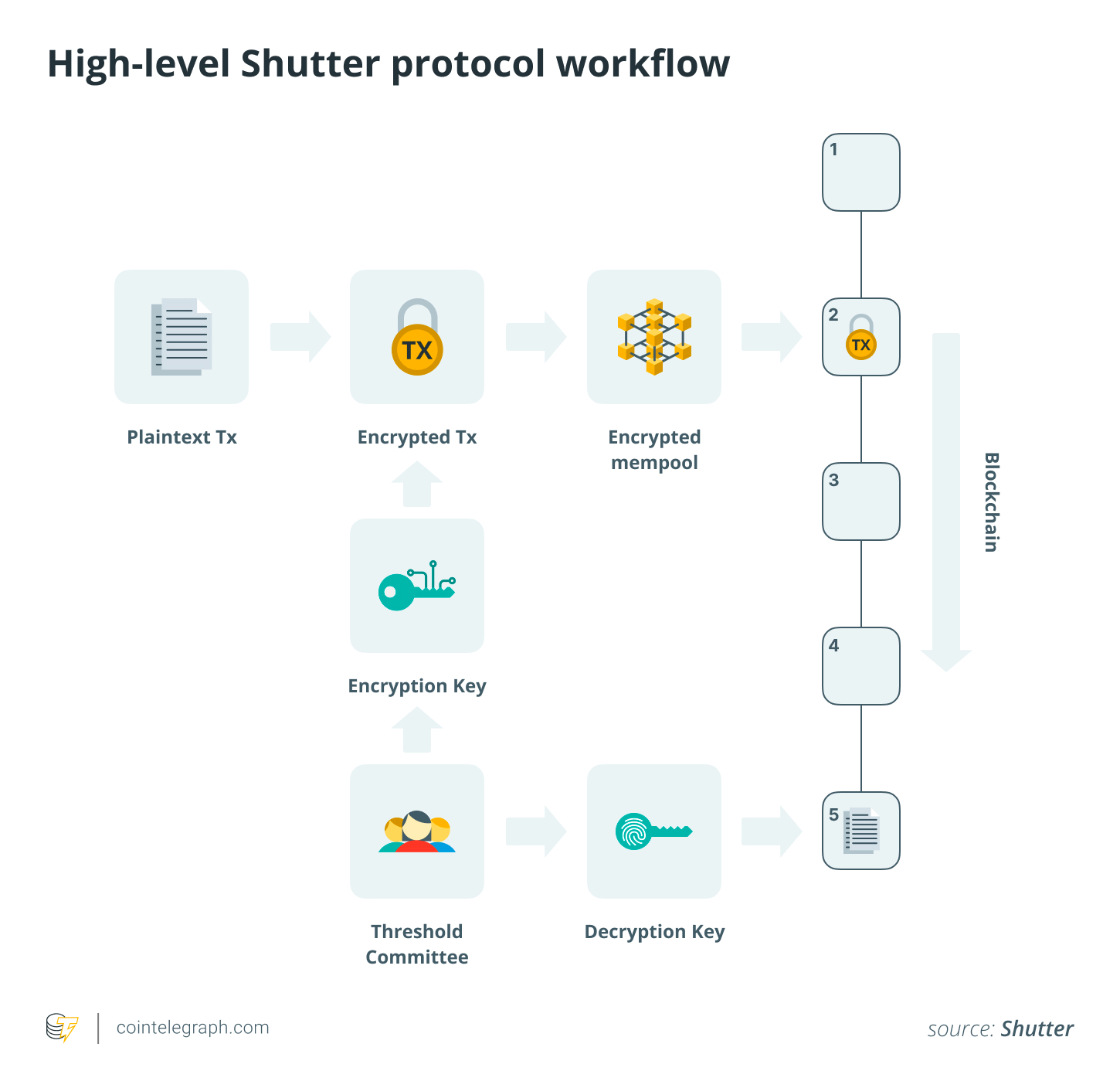
How Shutter Works: Protecting Your Transactions
Threshold encryption involves splitting a decryption key across a group of participants, known as Keypers. No single Keyper can decrypt a transaction on their own. When a user submits a transaction, it’s encrypted and sent to the network. Block proposers then order these encrypted transactions. Once a block is finalized, or a pre-defined condition is met, Keypers release their decryption shares. The combined shares then reveal the plaintext transaction, which is executed by the network’s virtual machine. This entire process acts as an offchain service, enhancing its compatibility across different blockchains.

Gnosis Chain and Beyond: Current Implementations
The Shutterized Beacon Chain on Gnosis Chain provides an alternative RPC endpoint where transactions are encrypted. While currently operational, there are considerations. Per-transaction encryption is employed, prioritizing simplicity over speed. The Shutter team is also developing an encrypted mempool module for the OP Stack, specifically on the Optimism testnet. This module addresses vulnerabilities present in the initial Shutter design and provides enhanced functionality.
Challenges and Future Outlook
Despite its promise, Shutter isn’t entirely trustless. Users must trust the Keyper set, which is a permissioned structure. Furthermore, the current deployment on Gnosis Chain faces latency challenges. The team is working towards a fully encrypted, trust-minimized mempool on Ethereum. This roadmap involves phased improvements across different areas. The team is considering the use of Batched Threshold Encryption (BTE) to minimize the load on Keypers. Ultimately, as MEV continues to evolve, solutions like Shutter will play a crucial role in fostering a more secure and equitable blockchain environment.


